What is the HTTP Authorization Header: Understanding Web Authentication Mechanisms
HTTP Authorization Header is an HTTP request header used for transmitting authentication credentials between the client and the server. It allows user agents (such as web browsers) to provide authentication information to the server in response to authentication requests.
HTTP Authorization Header is an HTTP request header used for transmitting authentication credentials between the client and the server. It allows user agents (such as web browsers) to provide authentication information to the server in response to authentication requests. Such requests typically occur when the server needs to verify if the requester has the right to access a particular resource. The Authorization header is one of the standard fields defined in the HTTP protocol, and its value usually contains credential information such as usernames and passwords, or a token such as OAuth or JWT (JSON Web Token).
In the field of web security, the HTTP Authorization Header plays a crucial role. By leveraging this header, servers can ensure that only authorized users can access sensitive data or perform specific operations. Whether it's regular web page access, web applications, API calls, or other HTTP-based interactions, preventing unauthorized access is a key component of maintaining system security. If credentials in the Authorization header are leaked or mishandled, it could lead to security vulnerabilities such as identity theft or data breaches, thereby threatening the security of the entire web application and user privacy.
Therefore, implementing and configuring appropriate authentication mechanisms, as well as ensuring the secure transmission and handling of the HTTP Authorization Header, is fundamental to protecting web resources from unauthorized access and is crucial in defending against network attacks such as man-in-the-middle attacks and replay attacks.
Detailed Explanation of HTTP Authorization Header
Definition and Purpose of the Authorization Header
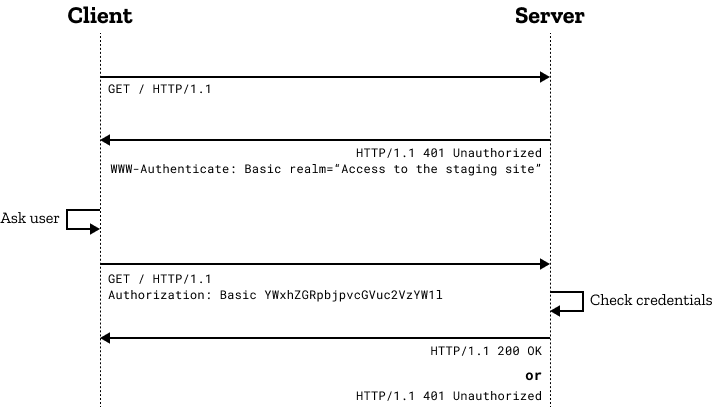
The HTTP Authorization request header is primarily used for clients to pass user authentication credentials to the server, such as usernames and passwords. Its format typically is:
Authorization: <type> <credentials>Where <type> represents the authentication type, indicating the authentication scheme being used, and <credentials> represents authentication credential information. When a web server needs to verify if the client request to access a resource is authorized, it usually includes a WWW-Authenticate response header in the HTTP 401 Unauthorized status to prompt the client for authentication. At this point, the client will use the Authorization header in subsequent requests to provide the necessary authentication information.
How to Use the Authorization Header for User Authentication
To use the Authorization header for user authentication, the client first needs to know the authentication type required by the server, typically provided through the WWW-Authenticate header in the 401 response. Then, the client constructs the appropriate credentials based on the authentication type.
For example, with Basic Authentication, the credentials would be a combination of a username and password, encoded into a Base64 string. The client places this encoded credential into the Authorization header and sends it back to the server for authentication.
Introduction to Different Authentication Mechanisms
Basic Authentication
Basic Authentication is the simplest HTTP authentication mechanism. It works by having the user agent send a Base64-encoded string of the username:password. Despite its simplicity, Basic Authentication is generally not considered secure because Base64 encoding is easily decoded, hence it's usually used in conjunction with HTTPS to ensure security.
Digest Authentication
Digest Authentication provides a higher level of security compared to Basic Authentication as it uses MD5 hashing to transmit passwords. Although more secure than Basic Authentication, Digest Authentication also has some security vulnerabilities and is less popular in modern web applications compared to other authentication mechanisms.
Token Authentication, such as Bearer Token
Token Authentication is a more secure authentication method widely used in current web applications, especially in RESTful API authentication. A common implementation is using Bearer tokens, where the client sends a key (token) that the server verifies and is usually a token identifying the user holding the key.
OAuth
OAuth is an open standard for authorization. It allows users to grant third-party applications access to their information stored on another service provider without directly providing usernames and passwords to the third-party application. OAuth can be used for authentication (OAuth 2.0) and authorization, such as allowing applications to access data on Google or Facebook on behalf of users.
API Keys
API keys are pre-generated sets of characters by the server that clients use as credentials to access API resources. API keys are typically sent as part of the request and can be placed in the URL, request header, or request body. Although API keys are convenient, they are more suitable for scenarios where security requirements are not particularly high and are often used in combination with other measures (such as restricting IP addresses) to enhance security.
Conclusion
The HTTP Authorization Header is a critical component of the HTTP protocol, supporting the authentication process of web applications. It allows clients to provide authentication credentials, usually in the form of usernames and passwords or information containing tokens and encrypted signatures, to facilitate the server in verifying the legitimacy of client requests. This mechanism is crucial for the security of websites and online services because it ensures that only users with appropriate permissions can access sensitive resources or perform specific operations.
Frequently Asked Questions (FAQ)
What authentication schemes does the HTTP Authorization Header support?
Common authentication schemes include Basic, Digest, Token (such as Bearer tokens, OAuth2), Hawk Authentication, and other custom schemes.
How to protect users' passwords when using the HTTP Authorization Header?
Passwords should not be transmitted or stored in plaintext when using the HTTP Authorization Header. HTTPS encryption should always be used for communication to prevent passwords from being intercepted during transmission. When storing passwords, they should be encrypted using hash functions (such as SHA-256) and possibly salted to enhance security.
What are the consequences if the HTTP Authorization Header is intercepted?
If authentication credentials are intercepted and data is not encrypted, attackers may exploit these credentials to access protected resources in the system. That's why using HTTPS strongly recommended, especially when performing sensitive operations. Additionally, some authentication schemes provide additional security measures, such as limiting tokens to specific sessions.
References
- RFC 7235 (Hypertext Transfer Protocol (HTTP/1.1): Authentication)
- MDN Web Docs - HTTP authentication
- OAuth 2.0 Authorization Framework
- Let's Encrypt

Learn more:
